Phishing, Smishing
Phishing
Everyone has dealt with this email annoyance. According to knowbe4, Phishing is the process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity using bulk email which tries to evade spam filters.
Some scammer in Nigeria sends an email that looks like this:

Then, some poor soul invariably clicks the ‘click here’ link, which leads to a spoofed login page. They enter their credentials into the adversary owned domain because it ‘looks the same’. If they’re unlucky enough, it will be a work email account. Even worse, if they reused the same password and somewhere else. This is your standard low hanging fruit credential harvesting phish. It’s used often, because it works.
Enter, a standard level of protection, two-factor or multi-factor authentication. I’m not going to go into the specific differences, but suffice to say, it involves ‘something you know’ (your password) and ‘something you have’ (some type of uniquely generated token/identifier). There are a lot of issues with using SMS (text message) as two-factor auth. Techniques to bypass this protection includes SIM Swapping or an overzealous login based on targeted spear-phishing. One such tool that helps enable this type of two-factor auth bypass pishing, is Modlishka. Modlishka can easily bypass two factor authentication running on Gmail, YahooMail, RadiffMail, Facebook etc and catch the credentials like username, password, two factor authentication token.
Smishing
Smishing is a portmanteau of “SMS” (short message services, better known as texting) and “phishing.” While not directly related to the above two-factor authentication bypass, Smishing is a growing portion of fraudulent communications; there’s just not as many protections around SMS, as there is for email. Smishing simply uses text messages as the delivery for a lure instead of email.
As more and more people use their personal smartphones for work (a trend called BYOD, or “bring your own device”) smishing is becoming a business threat as well as a consumer threat. So it should come as no surprise that smishing has been on the rise.
Examples of Smishing
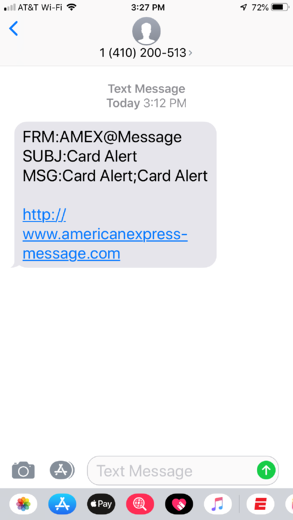
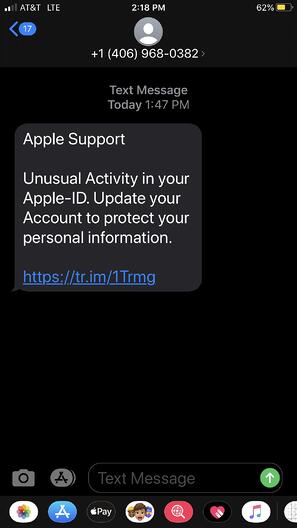
Most people know something of the risks of email fraud and learned, through training, to be suspicious of emails that say “click this link”. Bonus points if it is a generic content email, without any actual personal message from the supposed sender. Users are generally less wary when it somes to text messages, and there are less protections on a mobile device.
Phone numbers are much easier to spoof than email senders. Phone numbers are predictable and don’t even require any hacking or a leak, to capitalize on. So its’s easier for a spammer to ramp up, and start sending malicious links to a large swathe of people. This combination has given rise to fraud through SMS/Text messaging.
What can be done about curbing these types of attacks?? Training . Users must be trained to spot phishing attempts and report or ignore accordingly.
These problems are cat vs mouse situations, and no matter how good your defenses are, humans are always the weakest link. Information Security practitioners must conduct phishing training and awareness exercises for all users. The goal is to help make users aware of phishing attempts, and ideally, report these attempts so they can be blocked, or stopped in the future. Stopping phishing is not realistic, and it’s just not going to happen. However, by training users to spot red flags with suspicious emails and reporting it, the damage can be minimized.
Training
There are many different methods, tools, and companies that will help craft campaigns and metrics to train users. For my purposes, I use king-phisher by TrustedSec. It can be self hosted, with a client and server portions, and is highly customizable.
King Phisher is a tool for testing and promoting user awareness by simulating real world phishing attacks. It features an easy to use, yet very flexible architecture allowing full control over both emails and server content. King Phisher can be used to run campaigns ranging from simple awareness training to more complicated scenarios in which user aware content is served for harvesting credentials.

Out of the box, KingPhisher will help you craft phishing lures, web server landing pages, and track metrics of the campaign. It is focused on email address based phishing, with great support for sending and tracking methods. KingPhisher is extensible with plugins, one of which, clockwork-sms claims to send text messages for your target list. Between the cost of using clockwork, and the method (sends the text message via the carrier email gateway, eg ###-###-####@carrier.tld), I decided not to use the plugin. Some of the limiations are of course the cost, but needing to know the target carrier to craft the recipent ‘email’. Sending via this method also makes the text message stand out with content including ‘FRM’, ‘SUBJ’, and ‘MSG’ identifiers. (see example 1) I wanted a method that would actually use and send via SMS and not parsing to an email address.
I decided to use signalwire for the robust API access, and great prices. Unfortunately, there was no built in method with KingPhisher to utilize a different provider for purely SMS/smishing. Yet another entry point; plugins! I started with clockwork_sms.py as a baseline, to refactor into a signalwire plugin. Some major differences include, requiring more information for the signalwire API, and being sent via HTTP API versus an email gateway. This allows the text message to look like a normal standard text, because it is! (see example 2) The plugin sets the primary configuration options for signalwire, and a signal hook for the message-send from KingPhisher core. In addition to the plugin, this method required modification of KingPhisher core project itself to support ‘SMS’ only phishing.
Plugin
First things first, you’ll need to signup for a signalwire account. Signalwire has a python library for ease of use, installed through pip, and great documentation to get started quickly. pip install signalwire, and then test some code to make sure it works:
from signalwire.rest import Client as signalwire_client
client = signalwire_client("YourProjectID", "YourAuthToken", signalwire_space_url = 'example.signalwire.com')
message = client.messages.create(
from_='+15551234567',
body='Hello World!',
to='+15557654321'
)
print(message.sid)
After getting that test code working, it was time to create the KingPhisher plugin! Using clockwork as a base file, I modified it to be more inline with signalwire expectations. This included adding in plugin options for the signalwire api key, project id, and space url:
options = [
plugins.ClientOptionString(
'api_key',
'SignalWire API Key',
display_name='SignalWire API Key'
),
plugins.ClientOptionString(
'project_id',
'SignalWire Project ID',
display_name='SignalWire Project ID'
),
plugins.ClientOptionString(
'space_url',
'SignalWire Space URL',
display_name='SignalWire Space URL'
),
plugins.ClientOptionString(
'from_phone',
'SignalWire FROM Number, without "+" but including country and area code',
display_name='SignalWire FROM Number'
)
]
Then, you need to change the initialization to register the message-send signal, and status check for signalwire:
def initialize(self):
mailer_tab = self.application.main_tabs['mailer']
self.signal_connect('send-precheck', self.signal_send_precheck, gobject=mailer_tab)
self.signal_connect('message-send', self.signal_message_send, gobject=mailer_tab)
return True
def _get_status(self):
api_key = self.config['api_key']
project_id = self.config['project_id']
space_url = self.config['space_url']
try:
sms_client = signalwire_client(project_id, api_key, signalwire_space_url = space_url)
account = sms_client.api.accounts(project_id).fetch()
self.logger.info("Verified connection to '%s', status is '%s'\n" % (account.friendly_name,account.status))
if account.type != "Full":
self.logger.warning("Your SignalWire account is 'Trial' only! You will not be able to send messages to unverified phone numbers")
except:
self.logger.warning('Failed to connect to signalwire API', exc_info=True)
return None
return account.friendly_name, account.status, account.type
Finally, the plugin needs signal_message_send function that does the actual sending of the text message, through the signalwire API:
def signal_message_send(self, mailer_tab, target, message):
text_insert = mailer_tab.tabs['send_messages'].text_insert
if self._sms_number_regex.match(target.email_address) is None:
text_insert("Number '{0}' is not a valid phone number. Not sending!\n".format(target.email_address))
return False
api_key = self.config['api_key'].strip()
project_id = self.config['project_id'].strip()
space_url = self.config['space_url'].strip()
from_number = self.config['from_phone'].strip()
client = signalwire_client(project_id, api_key, signalwire_space_url = space_url)
msg = client.messages.create(from_="+{0}".format(from_number), body=message, to="+{0}".format(target.email_address))
text_insert("Msg ID '{0}' from '{1}' to '{2}', {3}.\n".format(msg.sid, from_number, msg.to, msg.status))
if msg.status == 'failed':
text_insert(msg.error_message)
return False
return True
All combined, these changes make up the basic signalwire SMS plugin. A few other checks and balances will need to be done for the reader to have a complete working plugin. (I don’t want to make it too easy for spammers and script kiddies!)
Core changes
For this project, I needed to alter the client core portion of KingPhisher, to accomodate pure SMS phishing. These changes include:
- adding regex checking for a proper 10 digit phone number _(reading from the emailaddress field, for simplicity)
- HTMLFilter to convert the message template from HTML, to plaintext
- adding a new ‘message type’ to the king phisher client UI, for ‘SMS’
- various checks to skip/ignore MIME message, and SMTP connections if message type is ‘SMS’
- adding the new ‘sms’ message type to config saving and loading functions
NOTE: specific code changes to KingPhisher core are not included in this post.
The front-end change for the UI is pretty simple, just adding a few lines:
+++ /opt/king-phisher/data/client/king_phisher/king-phisher-client.ui
@@ -7970,6 +7970,23 @@
<property name="position">1</property>
</packing>
</child>
+ <child>
+ <object class="GtkRadioButton" id="MailSenderConfigurationTab.radiobutton_message_type_sms">
+ <property name="label" translatable="yes">SMS</property>
+ <property name="visible">True</property>
+ <property name="can_focus">True</property>
+ <property name="receives_default">False</property>
+ <property name="tooltip_text" translatable="yes">Send SMS/Text messages</property>
+ <property name="draw_indicator">True</property>
+ <property name="group">MailSenderConfigurationTab.radiobutton_message_type_email</property>
+ <signal name="toggled" handler="signal_radiobutton_toggled_message_type" swapped="no"/>
+ </object>
+ <packing>
+ <property name="expand">False</property>
+ <property name="fill">True</property>
+ <property name="position">2</property>
+ </packing>
+ </child>
</object>
<packing>
<property name="left_attach">1</property>
Conclusion
These settings and sending could probably be incorporated directly into KingPhisher, without need for a plugin. With this setup, there are definitely still some caveats to sending SMS messages.
- You can’t leave the signalwire SMS plugin enabled when sending a phishing email campaign
- Signalwire plugin has to be loaded if the ‘SMS’ message type is selected, or the entire thing fails
- Because sent messages are queued to signalwire, there’s no real way to confirm the message was delivered
- Unless you query for the message SID after its sent to signalwire, which I skipped here
- Unless you query for the message SID after its sent to signalwire, which I skipped here
All in all these changes together helped me achieve the goal for training and awareness of SMISHING. I was able to modify KingPhisher to send SMS directly, through signalwire API, instead of an email -> SMS gateway. This was certainly a learning experience, from how KingPhisher plugins work, to the internals, and the complexities of phone numbers and SMS delivery.
From here, it’s just a matter of creating your target list, substituting the target phone number in the ‘email_address’ column instead of an email. Craft your lures, and remember the message should be fewer than 160 characters, including the link; and hit send!
Remember, only use this information for good! Have fun with your phishing.
Proudly written with VIM, pushed to gitea and processed with golang static site generator